Three steps to enhance Adabas data security on IBM Z®
Adabas on IBM Z can deliver unparalleled security and reliability. Take the steps now to protect your investment and build on your legacy.

IBM® Z platforms are known for security, and for good reason.
Most mainframes contain decades’ worth of valuable information including financial data, personal files and proprietary business material. When you look to maximize the value of Adabas & Natural applications on IBM Z, security can be just as important as performance and reliability.
IBM has been a pioneer in applying hardware-based encryption for business users. When you combine IBM’s pervasive encryption for the IBM Z with security-minded processes, the mainframe can offer broad coverage for your sensitive data.
“In a world where companies are threatened by cyber-attacks every day, security is no longer an afterthought, it’s a requirement. Data protection must play a vital role in your strategic IT plans. The risk of lost data can cripple an organization’s financial stability, jeopardize the credibility of an institution, and affect the competitive position of an organization, or worse,” says Michael Jordan, IBM Distinguished Engineer for Z Security.
The strengths of hardware-based encryption may lull some organizations into thinking the IBM Z is nearly invincible. But the security risks facing your enterprise systems are increasing daily because your mainframe is more exposed than ever. More tools and applications are accessing and manipulating volumes of data for analysis, intelligence and real-time processing. Enterprise systems are also more interconnected, with businesses relying on networks and the internet for daily operations.
Because of new and evolving threats, we recommend three steps to enhance security:
- Implement IBM Z Pervasive Encryption for encryption and key management
- Protect Adabas data sets at rest, in use and in flight
- Gain full visibility into all Adabas activity to detect unauthorized access
Let’s take a closer look at each step.
Step 1: Implement IBM pervasive encryption
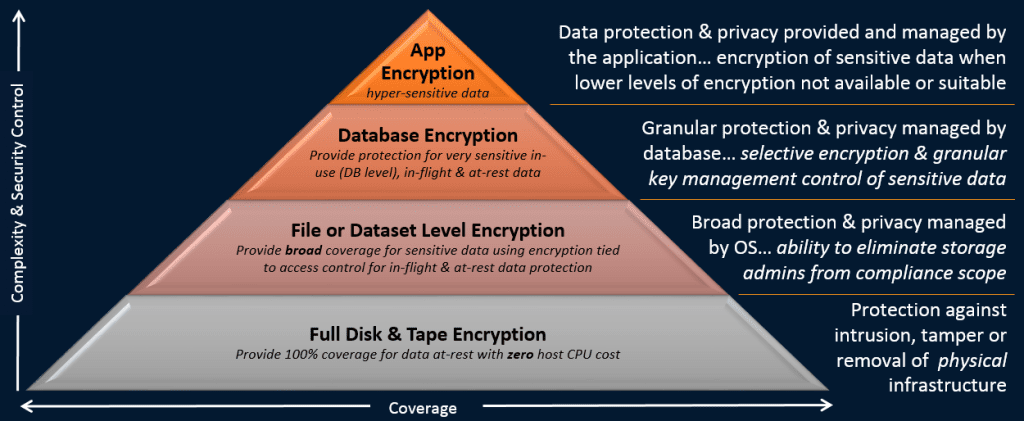
IBM’s security pyramid illustrates the scope of its pervasive encryption capabilities. At the base, organizations can use full disk and tape encryption to prevent loss of data in the event an unauthorized party walks off with your physical media. One level up, IBM’s file or dataset-level pervasive encryption delivers broad coverage linked to access control for in-flight and at-rest data protection. Both levels of security are necessary to secure your valuable Adabas data.
According to Jordan: “Extensive use of encryption is one of the most impactful ways to help reduce the risks and financial losses of a data breach and help meet complex compliance mandates.”

Step 2: Secure Adabas data
To protect your Adabas data, you need Adabas Encryption for z/OS. Adabas is highly optimized for I/O throughput, and as a result, IBM data set level encryption does not apply to Adabas natively. IBM and Software AG have worked closely together to create an optimal solution that extends IBM Pervasive Encryption to your choice of Adabas data sets while maintaining the fast database performance you rely on.
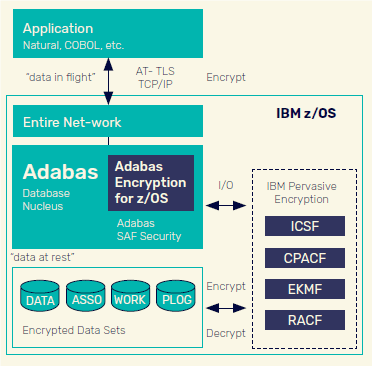

Adabas Encryption for z/OS enables you to take advantage of IBM’s strong, high-speed hardware-based encryption and centralized key management, while gaining additional capabilities tailored for Adabas. You can choose the extent of data encryption that suits your needs: encrypt your entire database, or just specific data sets. With the hardware-accelerated encryption on the IBM z14, z15 and z16 platforms—and the high throughput available on the z15 and z16—many users have the freedom to encrypt their entire database and keep performance high at the same time.
Like IBM’s dataset level encryption, Adabas Encryption for z/OS requires no changes to your applications. You can deliver uninterrupted data to authorized programs, users and services.
Combined with Adabas SAF Security to protect data in use, and Entire Net-Work to secure your data in flight, Adabas Encryption for z/OS enables you to deploy comprehensive security and protect your valuable data.
Step 3: Audit database activity
Finally, the third step in protecting Adabas data: Total visibility and auditability into database activity.
Adabas Auditing for z/OS delivers unprecedented insight into all your database activity, so you can better protect your valuable data and stay compliant with ever-growing data security regulations. Adabas Auditing for z/OS helps you know who is reading or changing your data, the changes made, when and where the activity occurred, and which applications accessed your data. Insights from Adabas Auditing for z/OS go far beyond simply comparing before-and-after changes. Instead, track and audit all commands for user files on the database including read, search, browsing, insert, delete and update commands for all user files on a database.
With an easy-to-use web-based solution, you can eliminate the need to build or customize your own Adabas z/OS audit tools – Adabas Auditing for z/OS is ready to use out of the box with all Adabas applications including Natural, COBOL, Assembler, PL/1 and Fortran. You can also safely archive indexed audit data for years or decades to comply with ever-growing regulations.
Learn more
Adabas on IBM Z can deliver unparalleled security and reliability. Take the steps now to protect your investment and build on your legacy.
This blog post has been updated. It was originally published on June 3, 2021.